|
|
|
3.1 Layer 1 (Physical) ConnectivityBefore any two components of your network can talk to each other, they must share a common physical medium through which they communicate. In the wired world, this is obvious; you would never try to connect a copper CAT5 cable to a piece of fiber and expect it all to "just work." In the wireless world, every device from your network to your cordless phone to your garage door opener must share the same physical medium: electromagnetic waves radiating through the air. It is possible for all of these devices to communicate without interfering with each other because they can be made sensitive to a particular portion of the vast electromagnetic spectrum. This is analogous to tuning channels on a radio or TV—many channels are broadcasting simultaneously, but they are well-coordinated and only use a portion of the available spectrum, to avoid interfering with each other. So before any other considerations, devices that need to intercommunicate on your network must be able to send signals in the same frequency range. Obviously, an 802.11b card operating at 2.4GHz doesn't have a chance of carrying on a conversation with an 802.11a Access Point speaking at 5GHz. In addition to using a particular frequency range, each wireless protocol also defines a plan for using that range. For example, the original 802.11 specification defines two RF modulation schemes, FHSS and DSSS. Both operate at 2.4GHz, but use the spectrum differently. Frequency Hopping Spread Spectrum (FHSS) breaks the available spectrum into 77 channels, each 1MHz wide. It uses a time-based, pseudo-random algorithm to quickly skip between all of the available channels in an attempt to avoid noise from other 2.4GHz devices. As we saw in Chapter 2, Direct Sequence Spread Spectrum (DSSS) breaks the same frequency range into 11 overlapping channels, each 5MHz apart (but 22MHz wide). It uses one channel at a time and employs more sophisticated encoding techniques to avoid noise and increase the data rate. Although FHSS and DSSS devices both operate "at 2.4GHz," they have no hope of being able to communicate with each other. Whatever wireless equipment you choose, be sure that both ends are capable of speaking the same protocol at the same frequency range, whether that's 802.11b speaking DSSS at 2.4GHz, 802.11a speaking OFDM at 5GHz, 802.11g speaking OFDM at 2.4GHz, or something altogether different, new, and wonderful. If two pieces of equipment claim compatibility with the same IEEE standard (such as 802.11b), they should theoretically be able to interoperate. Be sure to check the fine print on any device that only claims compatibility with an umbrella term (such as Wi-Fi), because the definition of the term can change at the whims of marketing moguls.[1]
As 802.11b is by far the most common technology used in the wireless community effort, we will focus on its particulars for the rest of this chapter. 3.1.1 Layer "1.5" ConnectivitySimply using equipment that adheres to the same standard on the same channel doesn't quite fulfill the requirements of Layer 1 (physical) connectivity. There are a few more protocol requirements that must be met before we can move on to Layer 2. 802.11b defines two possible (and mutually exclusive) radio modes that stations can use to intercommunicate. Those modes are BSS and IBSS. BSS stands for Basic Service Set. In this operating mode, one station (the BSS master, usually a piece of hardware called an access point, or AP) provides wireless-to-Ethernet bridging. Before gaining access to the wired network, wireless clients (also called BSS clients) must first establish communications with an access point within range, as shown in Figure 3-1. Once the AP has authenticated the wireless client, it allows packets to flow between the client and the attached wired network, either routing traffic at Layer 3, or acting as a true Layer 2 bridge. A related term, Extended Service Set (ESS), refers to a physical subnet that contains more than one AP. In this sort of arrangement, the APs can communicate with each other to allow authenticated clients to "roam" between them, handing off IP information as the clients move about. Note that (as of this writing) there are no APs that allow roaming across networks separated by a router.[2]
Figure 3-1. In BSS (or ESS) mode, clients must associate with an AP before accessing the wired network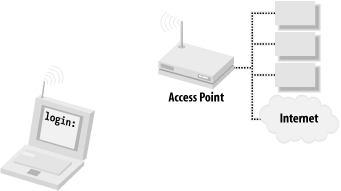 IBSS stands for Independent Basic Service Set, and is frequently referred to as ad-hoc or peer-to-peer mode. In this mode, no hardware AP is required. Any network node that is within range of any other can communicate if both nodes agree on a few basic parameters. If one of those peers also has a wired connection to another network, it can provide access to that network. Figure 3-2 shows a model of an IBSS network. Figure 3-2. In IBSS mode, nodes can talk to any other node within range; a node with another network connection can provide gateway services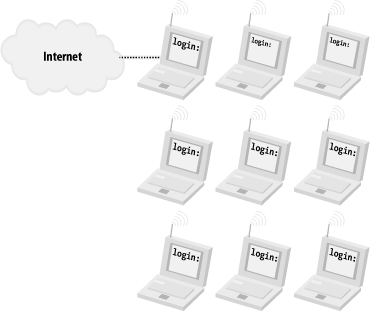 Note that an 802.11b radio must be set to work in either of these modes, but cannot work in both simultaneously. Both modes support shared-key WEP encryption (more on that later). I give specific examples of how to set up BSS and IBSS networks in Chapter 4 and Chapter 5. Once you have two or more IBSS mode stations, or a BSS master and one or more BSS clients all within range, you are ready to move on to actual networking. 3.1.2 Layer 2 and UpOnce the physical layer is established, a wireless network is very much like a traditional Ethernet network. Assuming that you want to connect your wireless clients to the Internet, you'll want to provide all of the usual TCP/IP services that make networking so much fun (such as DNS and DHCP). To the rest of your network, wireless clients look like just another Ethernet interface, and are treated no differently than the wired printer down the hall. You can route, rewrite, tunnel, fold, spindle, and/or mutilate packets from your wireless clients just as you can with any other network device. Once wireless packets hit the wire, you use the same hubs, switches, and routers that make up the majority of traditional wired networks. |
|
|
|