| [ Team LiB ] |
|
1.1 OriginsThe word Kerberos originates from Greek mythology, which contains the legend of Cerberus. Cerberus guarded the realm of the underworld, ruled by Hades and his wife, Persephone. What Cerberus looked like depends on whom you ask; Hesiod claims that Cerberus has fifty heads, while Apollodorus describes him as a strange mixture of creatures with three dog-shaped heads, a serpent as a tail, and heads of snakes over his back. Cerberus is most often pictured as a creature with three heads. Either way, Cerberus was a vicious creature that few dared to challenge. The Greeks believed that when a person dies, his soul is sent to Hades to spend eternity. While all souls were sent to Hades, those people who had led a good life would be spared the eternal punishment that those who had not would have to endure. Cerberus, as the gatekeeper to Hades, ensured that only the souls of the dead entered Hades, and he ensured that souls could not escape once inside. As the gatekeeper to Hades, Cerberus authenticated those who attempted to enter (to determine whether they were dead or alive) and used that authentication to determine whether to allow access or not. Just like the ancient Cerberus, the modern Kerberos authenticates those users who attempt to access network resources. Like every other great figure in mythology, Cerberus had a fatal flaw that enabled some clever people to pass through Cerberus to Hades. We'll revisit the legend and discuss one such story and its modern counterparts in Chapter 6. Finally, if the ancient mythological character was named Cerberus, why is the modern authentication system called Kerberos? Simply put, they are just different spellings of the same word. In order to provide a distinction between the ancient mythology and the present-day software system, we will refer to the mythological character as Cerberus and the modern software system as Kerberos. 1.1.1 Modern HistoryThe modern-day origins of the Kerberos network authentication system are a bit more mundane than the ancient mythology of Cerberus. Kerberos began as a research project at the Massachusetts Institute for Technology (MIT) in the early 1980s. The MIT faculty at the time recognized that the explosion of widely available, inexpensive computers would transform the computing industry. 1.1.1.1 The time-sharing modelTraditionally, computers were a large, expensive, and centralized resource that end users accessed through dumb terminals connected via serial lines. This is called the time-sharing model (Figure 1-1). Figure 1-1. Time-sharing model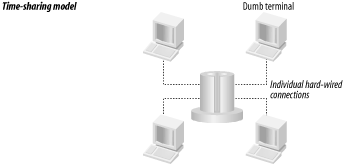 The time-sharing model had some distinct administrative advantages. Since there was only one (albeit large) computer, maintaining user accounts and privileges was easy. To add a user account, the administrator simply created an entry in the machine's password file and the user immediately had access. Deleting accounts or changing passwords was similarly easy; there was a single point of administration by definition, since there was only one machine involved. In addition, the time-sharing model had no need for encryption of passwords during transit. Users connected to the machine via dedicated serial lines, and each user had their own dumb terminal connected to their own serial line. Since the communication medium was not shared, one user could not listen into the communications of another user without physically tapping their serial wire. 1.1.1.2 The client-server modelThe advent of the packet-switched computer network dramatically changed how users interfaced with computers. With the computer network, users all had an inexpensive computer on their desk, connected to all of the other computers in the organization through the network. Since the desktop computers still were not very powerful, specialized, more powerful server computers were used to provide services such as file storage, printing, and electronic mail to users. This new computing model, widely referred to as client-server, provided some distinct advantages to both users and administrators (Figure 1-2). End users enjoyed increased usability since the desktop computers, while not very powerful, were powerful enough to present menu-driven interfaces to the resources of the server machines; a marked improvement over typing cryptic commands on a dumb terminal or line printer. Figure 1-2. Client-server model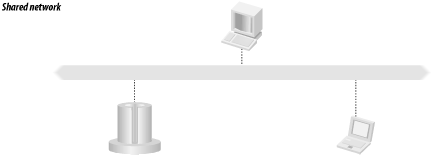 However, the faculty at MIT recognized that this new model required a dramatic new software architecture and a new way of thinking about computing: a way of thinking that recognized that computing power, rather than being centralized, was now distributed throughout the entire campus. A major problem that the advent of personal computers and the network presented was that the end-user clients could no longer be trusted. In the traditional time-sharing model, end users only had a dumb terminal, which had no processing power at all. Since the computer all of the users shared was under the total control of the system administrators, it could be trusted. Now, with inexpensive personal computers on all of the end-users desks, the system administrators no longer had total control over all of the computing power; indeed, end users could modify any part of the software on their personal machine they wanted, going as far as replacing the operating system itself. Since the end users now controlled their own computer, they could spoof messages to other machines, listen in on connections between other machines on the network, and impersonate the identities of other users. 1.1.1.3 Project AthenaEnter Project Athena. Project Athena was established with support from a consortium of computer vendors in May 1983 with a five-year timeline. Athena's focus was to develop strategies and software for integrating computers into MIT's curriculum. In particular, Athena was designed from the start as a networked, client-server system. While Project Athena had a decidedly educational focus, the end result included several software packages that are still in wide use today. As mentioned earlier, passing passwords over a network in clear text is akin to shouting in a crowded room. However, that is exactly how software of the day functioned: the standard remote login protocols such as Telnet and rlogin sent user credentials over the network in clear text. Even worse, other server software, such as rlogin, blindly believed the identity that the client computer sent to it. Thus, unscrupulous users could (trivially) write fake rlogin clients that would be able to impersonate anyone else on the network. This was unacceptable in an academic environment, where dishonest users could listen to network messages for other users' passwords or steal others' work. In addition, the now decentralized nature of the computing resources presented the problem that every user had access to several computers on the network, each requiring its own username and password. This model contrasted with the older timesharing model, in which end-user machines were connected to one centralized computer via a dedicated serial line, and only one login was required. To solve these problems, Project Athena developed the Kerberos protocol for network authentication. The Project Athena Technical Plan outlined the major goals of the new service; namely, to extend the services of authentication typically found in large time-sharing systems to a distributed network consisting of servers and untrusted end-user client machines. The new authentication system had to centralize the trust into machines that were tightly controlled and monitored, and encrypt any sensitive transactions between these authentication servers and other machines on the network. Many other packages also came out of the efforts of Project Athena. Project Athena developed the X Window System, which is now used as the basis for every Unix system's Graphical User Interface. Other packages that relate to distributed computing include the Hesiod distributed name service, and the Moira distributed network administration system. The combination of Project Athena and similar projects at other large universities across the U.S. and the world provided these institutions with advanced single-sign-on network infrastructure across all major network protocols, including electronic mail, file sharing, and even instant messaging. By using Kerberos and applications that support Kerberos authentication in your own network, you can achieve this goal as well. |
| [ Team LiB ] |
|