| [ Team LiB ] |
|
6.8 NetgroupsNetgroups have become a daily staple for NIS administrators. They allow machines and/or users to be collected together for various administrative tasks such as grouping machines together for use in the tcp_wrappers files /etc/hosts.allow and /etc/hosts.deny. In this next example, you restrict access via ssh only to members of the sysadmin netgroup: # /etc/hosts.deny sshd: ALL . . . # /etc/hosts.allow sshd: @sysadmin Netgroups can be composed solely of individual hosts: sysadmin (garion.plainjoe.org,-,-)(silk.plainjoe.org,-,-) or other netgroups: all_sysadmin sysadmin secure_clients or of any combination of the two. RFC 2307 describes the structural nisNetgroup object class (Figure 6-7), which can be used to represent netgroups as directory entries. The cn attribute holds the name of the netgroup, the nisNetgroupTriple attribute stores the (host, user, NIS-domain) entries, and the memberNisNetgroup attribute stores the names of any nested netgroups. Figure 6-7. nisNetgroup object classes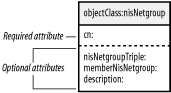 Before adding any netgroup entries to the directory, you must create the container ou. By convention, I will use the ou=netgroup organizational unit for storing netgroups in this example: dn: ou=netgroup,dc=plainjoe,dc=org objectclass: organizationalUnit ou: netgroup After passing through PADL's migrate_netgroup.pl tool, the sysadmin netgroup will be represented by this LDIF entry: $ ./migrate_netgroup.pl /etc/netgroup dn: cn=sysadmin,ou=netgroup,dc=plainjoe,dc=org objectClass: nisNetgroup objectClass: top cn: sysadmin nisNetgroupTriple: (garion.plainjoe.org,-,-) nisNetgroupTriple: (silk.plainjoe.org,-,-) The all_sysadmin netgroup contains the sysadmin and the secure_clients netgroups, so it will use the memberNisNetgroup attribute: dn: cn=all_sysadmin,ou=netgroup,dc=plainjoe,dc=org objectClass: nisNetgroup objectClass: top cn: all_hosts memberNisNetgroup: sysadmin memberNisNetgroup: secure_clients After adding these entries to your directory, you must configure the nss_base_netgroup parameter in /etc/ldap.conf to use the correct search suffix: ## /etc/ldap.conf ## <remaining parameters imitted> ## Configure the search parameters for netgroups. nss_base_netgroup ou=netgroup,dc=plainjoe,dc=org?one Finally, you must inform the the operating system to pass off netgroup queries to the LDAP directory by updating the netgroup entry in /etc/nsswitch.conf: ## /etc/nsswitch.conf ## . . . netgroup: ldap The getent tool can be used to query NSS for specific netgroups by giving the group name as a command-line parameter: $ getent netgroup sysadmin sysadmin (garion.plainjoe.org,-,-)(silk.plainjoe.org,-,-) It would also be a good idea to verify that the /etc/hosts.allow listed in the beginning of the section obeyed the netgroups membership by actually attempting to log on to the machine using ssh from a host other than garion or silk. There are many services that can use netgroups. The tcp_wrappers security package is only one example. Another frequent use of netgroups is to utilize them to restrict access to exported NFS file systems (refer to the exports(5) manpage). Any place where these administrative groups were used in your NIS domain should remain valid for these new nss_ldap-enabled systems. |
| [ Team LiB ] |
|